
|
|
If you close/exit NetVizor by clicking the "X" on the top right of the interface NetVizor will NOT resume monitoring and you will have to manually restart NetVizor and click "Start Monitoring" again.
Monitoring Mode - Standard Vs. Blackbox
This is the default monitoring mode. In standard mode NetVizor records all user activities and allows you to view them in real-time at any time via the NetVizor web interface, or the NetVizor viewer software. Logs are not encrypted (unless configured in the additional Security settings) and can be set to be stored locally, or on a network share. This monitoring mode allows you to view logs as they are created and respond immediately to logged events. Activity alerts operate in real-time. Blackbox / Reactive The blackbox monitoring mode records all user activities and stores them locally in an unreadable encrypted format for later viewing, if desired. Logs can only be viewed after being unlocked, and are retained only for a set number of days as configured. This monitoring mode allows you to honor the complete privacy of your network users while still being able to unlock logs for evidence in the event that an unwanted behavior occurs. Alerts are still transmitted in real-time, however, allowing you to react to threats as they occur. |
 To
Start Monitoring with NetVizor, click the "Start Monitoring"
button - then enter your NetVizor password.
To
Start Monitoring with NetVizor, click the "Start Monitoring"
button - then enter your NetVizor password.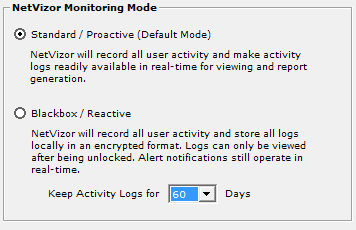 Configured by clicking on 'Activity Logging and Configuration' - 'Configure Monitoring Mode', 'NetVizor can operate in two different monitoring modes - standard/proactive, and blackbox/reactive.
Configured by clicking on 'Activity Logging and Configuration' - 'Configure Monitoring Mode', 'NetVizor can operate in two different monitoring modes - standard/proactive, and blackbox/reactive.